As you rethink your mobile security approach, make sure you stay compliant.

Simplify CDM & FISMA Reporting Requirements
Mandate Mania
Pursue Compliance with Confidence
Mandates are put in place for good reason. Protecting tracked personally identifiable information (PII), meeting configuration baselines, and preventing cybersecurity threats are all unquestionably important. But compliance adds pressure on both budget and staff resources.
Ivanti helps your agency meet these mandates, whether originating from the Office of Management and Budget (OMB) in the USA, your federal government’s equivalent office, state/provincial, or local government entities.
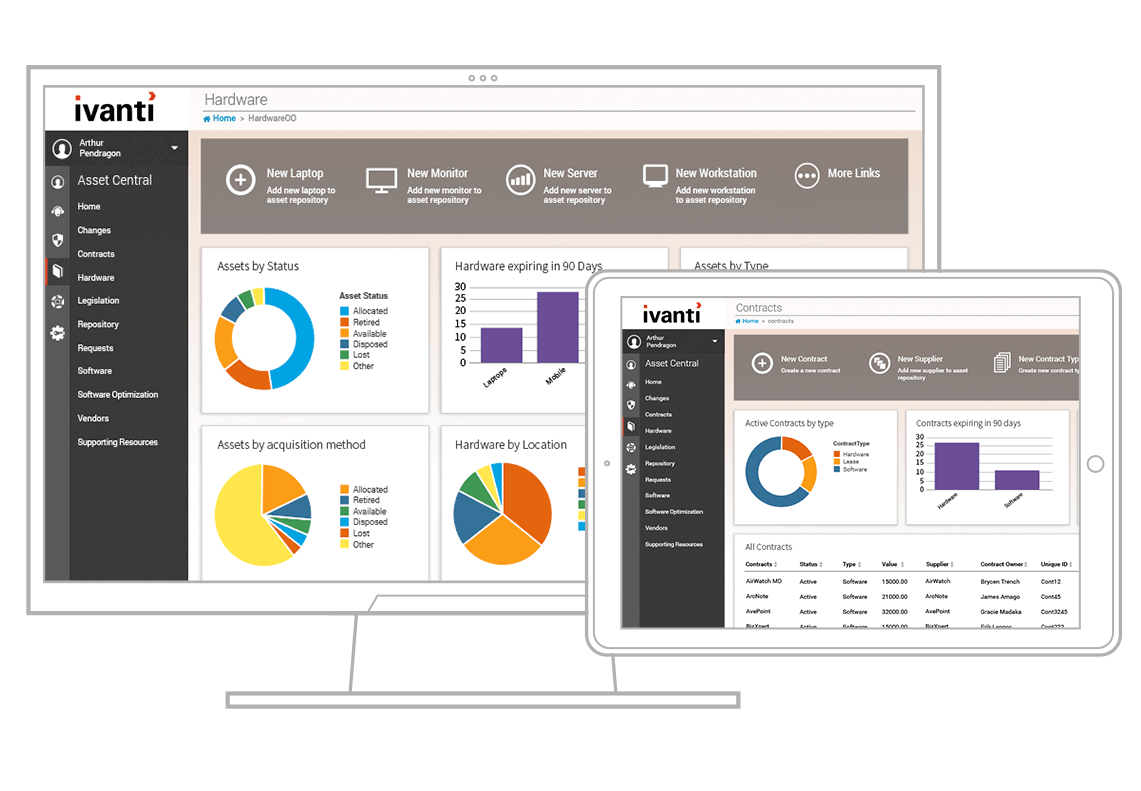
Know what you have, where and that it’s secure
Whether complying with FITARA, or international equivalents, visibility to the hardware and software estate is key to ensuring spend is going to the correct and necessary projects.
Protect Vital Systems
Comprehensive Reporting
Modern Service Management
Centralized Control
Stop the Evildoers
Compliance and Fiscal Responsibility
Yes, you can meet both objectives. Ivanti gives agencies the visibility and control they need to secure and protect citizens and data, while delivering a fast time-to-value on IT investments.
How we can help
Centralize, simplify, keep users happy, and bring all your data together. That’s Ivanti.
FedRAMP Authorized Platform
FedRAMP Authorized Platform
Cloud deployment to reduce ongoing administration requirements for ITSM/ITAM tools while speeding time for new functionality.
Unified Management Experience
Unified Management Experience
Establish intelligent, integrated control over your user’s multi-platform desktops and mobile devices keeping them updated and secure.
Know What You Have
Know What You Have
Asset lifecycle management capabilities to manage and optimize assets for security, performance, and cost.
Simplified Patching
Simplified Patching
Speed the time to remediate vulnerabilities, so IT can accomplish additional projects with existing staff.